It’s no longer a matter of ‘if’: Your business will be the target of a cyberattack.
With this reality comes the need for an “assume breach” mindset. What will you do the moment after you realize you are the victim of a successful incursion? Knowing how to answer that question means being able to detect threats early and deliver fast, fulsome recovery of internal systems in the event of an attack.
How do you make this possible for your organization? Increasingly, it means running response efforts from a cybersecurity clean room.
A cybersecurity clean room is a trusted environment where security analysts can perform forensic analysis of artifacts and assets related to cyber events. Having a secure IT environment, isolated from production networks (logically or physically), means the security team can go about the business of solving problems—without worrying about reintroducing malicious code and risking reinfection.
But the design, deployment, and maintenance of an isolated environment can be daunting. Indeed without executive support, many businesses struggle to justify the budget and staff required to build and maintain such a secure space. Rubrik and Mandiant recently announced a partnership to bolster resilience across the whole intrusion lifecycle, combining Rubrik’s data security and cyber resilience technology and Mandiant’s threat intelligence and incident response capabilities. This is a real game changer when it comes to building a secure environment for cybersecurity analysis.
But what does this look like in the real world? Let’s take a look at how to quickly and confidently recover to Google Cloud.
How-To: Clean Recovery With Google Cloud
Rubrik Security Cloud can serve as the data security control plane of a cybersecurity clean room orchestrating data protection and recovery of your vital business data—wherever it resides—to an immutable platform. It automatically monitors each backup taken against a best-in-class threat intelligence, including Google Threat Intelligence, identifying malware and threats from over 4000 threat groups. It analyzes each backup for the presence of sensitive and regulated data and monitors user access to that data, identifying potentially overprovisioned access and stale data that can pose a risk to your business. It leverages AI and machine learning to spot anomalous activity at the filesystem and hypervisor layer, so you can quickly determine if an attacker has been successful and the extent of the damage they have caused. Finally, it gives you a powerful tool to recover your business with confidence, through Cyber Recovery.
As Rubrik Security Cloud is out-of-band from production data, all of these components are logically separated from the greater IT environment. So if an attacker breaches your defenses, Rubrik Threat Monitoring, Anomaly Detection (or both) will alert you to the incursion.
Here’s what you do next:
First, lock down known bad snapshots with Threat Containment. Native role-based access control (RBAC) prevents potentially malicious snapshots from being reintroduced into production.
By connecting Rubrik Security Cloud to a Google Cloud VMware Engine (or GCVE) software-defined data center (SDDC), a security operator with the relevant privileges can quickly and easily recover these quarantined snapshots into a malware-free, clean environment isolated from production. These snapshots have significant value in forensic investigation (see below).
With the impacted servers identified (and hopefully, the snapshots quarantined) and Rubrik Security Cloud connected to the GCVE SDDC, the compromised snapshots can be easily selected in Cyber Recovery and recovered in the cloud SDDC, isolated from production. There is no requirement to have a recovery plan in place before an attack: the ability to respond on an ad hoc basis is vital for effective cyber recovery.
Once recovered, the security team (whether this is in-house, or a third-party incident responder, such as Mandiant) can get moving with their investigation, safe in the knowledge that this environment is safely isolated from production. Alternatively, you could take the recommended snapshots from Rubrik Security Cloud and spin them up in GCVE for final checks prior to recovering to production.
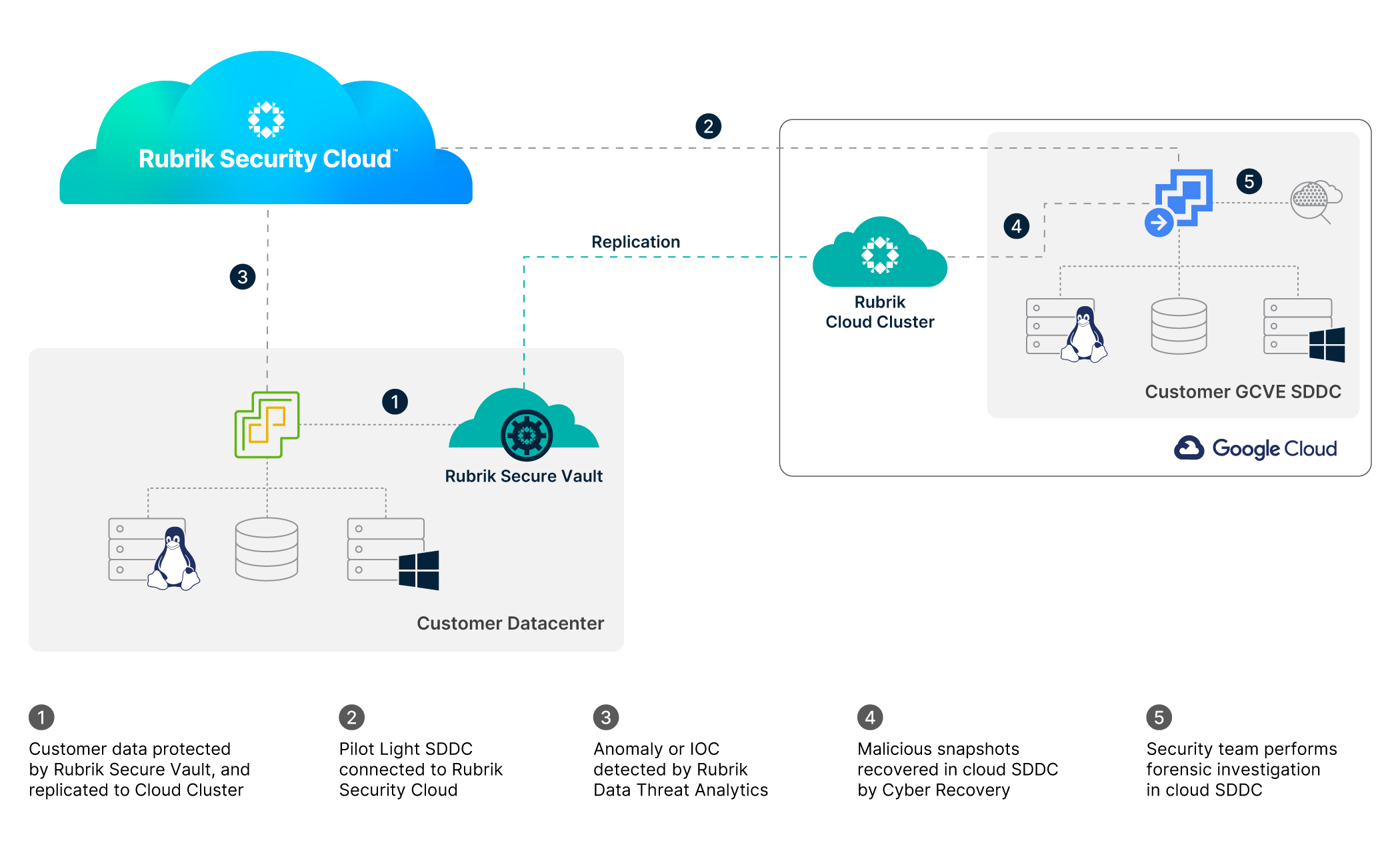
Depending on the outcomes of this investigation, you may be able to fully evict the attacker from production and use Rubrik Security Cloud to recover systems and data to a known clean state. In extreme situations, you may decide to take a scorched earth approach, where production is rebuilt from scratch. In this latter scenario, the cloud environment can be a perfect way to recover a minimal viable business to keep things running while other, less vital systems, services, and data are recovered.
Cybersecurity Clean Room: Next Steps
A cybersecurity clean room is an important part of a robust cyber resilience strategy, alongside an immutable data security platform, tooling to detect anomalies and threats, and orchestration to enable recovery at scale. While setting up and maintaining a clean room can be daunting and costly, Rubrik and Google Cloud have combined forces to make it simple to set up a clean room in the cloud.
Check out Rubrik Cyber Recovery now, with this click-through demo!
Safe Harbor Statement: Any unreleased services or features referenced in this document are not currently available and may not be made generally available on time or at all, as may be determined in our sole discretion. Any such referenced services or features do not represent promises to deliver, commitments, or obligations of Rubrik, Inc. and may not be incorporated into any contract. Customers should make their purchase decisions based upon services and features that are currently generally available.
